


In September 2022, global headlines exploded when Uber confirmed a major cybersecurity breach orchestrated by an 18-year-old hacker. In what felt like a scene from a novel, the teenager leveraged social engineering tactics to deceive an Uber contractor and obtained access to the company’s HackerOne bug bounty account, Slack communication channels, and critical cloud infrastructure including AWS and Google Cloud systems. The hacker even posted a message on Slack that read: “I announce I am a hacker and Uber has suffered a data breach,” a message that instantly went viral as screenshots began circulating across Twitter.
For Uber, the embarrassment was global. But the bigger lesson was clear: if a trillion-dollar company with cutting-edge security can be breached by a teenager, what chance does an average business stand?
This wasn’t just a cyber incident. It was a wake-up call.
Today, in 2025, cyber threats have evolved far beyond stolen passwords or leaked emails. They are existential risks capable of disrupting economies, crippling supply chains, and eroding customer trust in a matter of minutes.
The truth is harsh: a business somewhere in the world falls victim to a cyberattack every 11 seconds.
The question leaders must ask is no longer “Will we be attacked?” but “When it happens, will we be ready?”
In this article, I will list the top 10 Cybersecurity threats in the world with clear case studies.
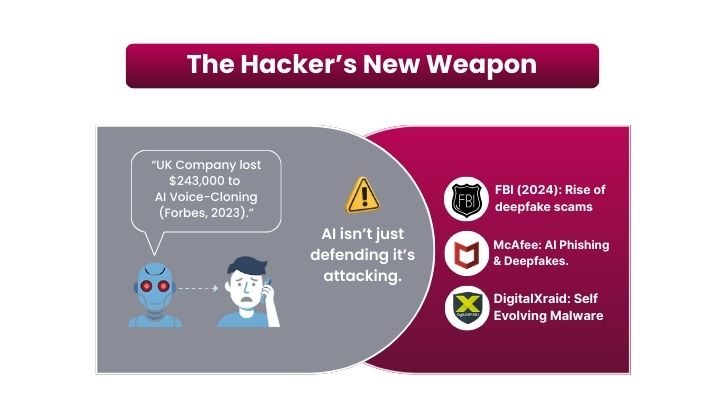
In 2023, fraudsters used AI voice-cloning to impersonate a CEO and trick a UK company into transferring $243,000 Forbes . A phone call that sounded real was enough to move nearly a quarter of a million dollars.
AI is no longer just a defensive tool, it has become a weapon for cybercriminals. In 2024, the FBI warned that threat actors were increasingly using deepfake audio and video to impersonate executives and scam organizations.
AI isn’t just helping defenders, it’s empowering attackers too:
With AI making phishing, deepfakes, and reconnaissance faster and more convincing, traditional defenses alone are no longer enough. Organizations must adopt AI-driven security tools and continuous employee awareness training to stay ahead of evolving threats.
In 2021, the Colonial Pipeline ransomware attack forced the shutdown of fuel delivery across the U.S. East Coast. The shutdown triggered panic buying and supply disruptions, leading the company to pay a $4.4 million ransom to resume operations. Federal agencies including the DOE and FBI, responded rapidly to coordinate mitigation efforts
Today’s ransomware has evolved into Ransomware 3.0—a more dangerous and multi-dimensional threat:
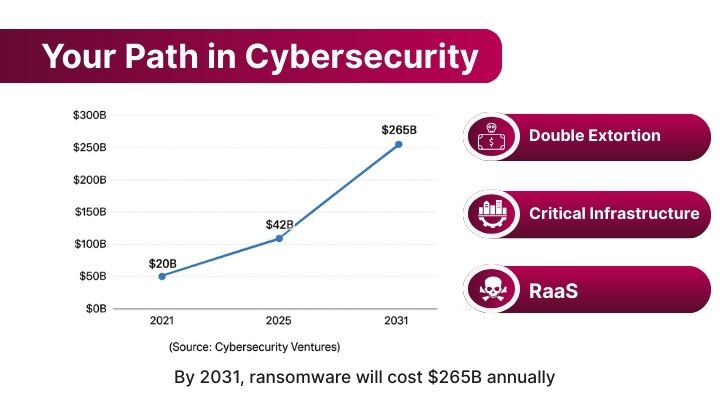
Projections indicate that by 2031, ransomware could cost businesses $265 billion annually, underscoring the growing scale of this threat Cybersecurity Ventures.
Ransomware 3.0 is no longer just about locked files—it’s about deep operational damage, data blackmail, and weaponized convenience for threat actors.
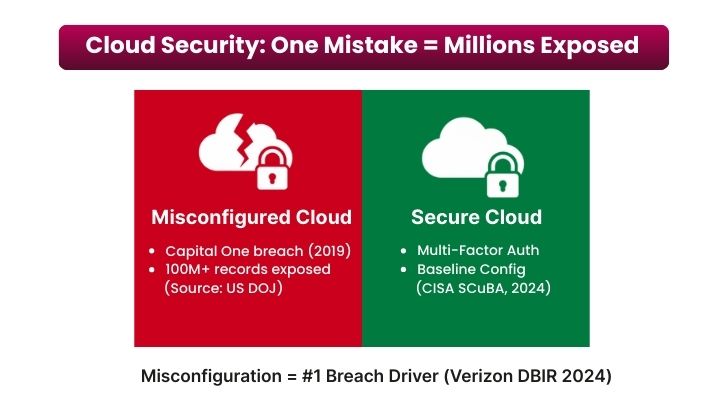
One configuration mistake can expose millions of records. A clear example: the Capital One breach (2019), where an attacker exploited a misconfigured web application firewall to access sensitive data; U.S. prosecutors documented the misconfiguration in the case record (U.S. Department of Justice).
Why this remains a top threat:
Billions of internet-connected devices (cameras, routers, sensors) still ship with weak defaults and limited patching. Attackers routinely conscript them into botnets for large-scale disruption.
Mirai (2016): the creators of the Mirai IoT botnet pled guilty after using default-credential devices to launch massive DDoS attacks that knocked major services offline U.S. Department of Justice. A separate DOJ case detailed how the October 2016 IoT attack caused “massive disruption to the Internet
Why it’s still a top risk:
Not all threats come from outside. Employees or partners can cause big damage.
Case in point — Tesla (2020): A Russian national offered a Tesla employee $1 million to install ransomware; the employee reported it and the FBI disrupted the plot.
For context, the Verizon 2024 DBIR shows insiders remain a material share of breaches across sectors.
Executive takeaway: Limit access (least-privilege), monitor behavior, and follow CISA’s insider-threat guidance to reduce exposure.
Your vendors and partners can be your weakest link.
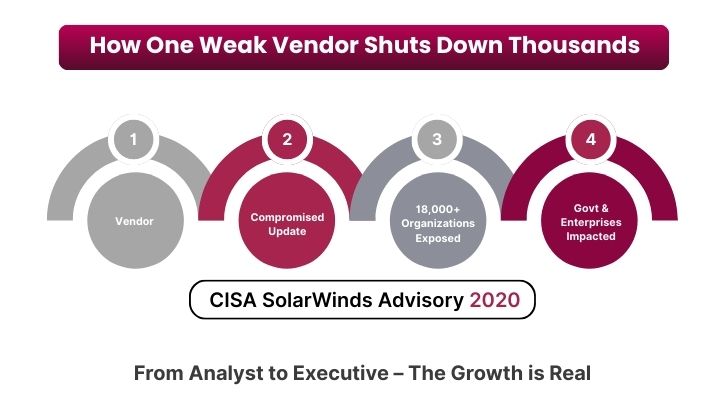
SolarWinds (2020): Hackers injected malicious code into the widely used Orion software updates, compromising approximately 18,000 organizations, including government agencies and private firms.
Gartner warns that by 2025, 45% of organizations worldwide will experience software supply chain attacks, a sharp rise from previous years Gartner Press Release.
Attacks on essential services can disrupt entire nations.
Colonial Pipeline (2021): A ransomware attack forced the shutdown of the largest U.S. fuel pipeline, leading to fuel shortages across the East Coast. The DOJ later seized part of the ransom paid to the attackers.
Cybercriminals often bypass technology by targeting people. Manipulation tactics like phishing, voice cloning, and fake emails can cause millions in losses.
Toyota Boshoku (2019): Criminals tricked staff into wiring $37 million to fraudsters using a fraudulent money transfer request. The company publicly confirmed the incident in its disclosure Toyota Boshoku Statement.
A zero-day vulnerability is a flaw that is exploited before developers release a fix. These threats leave organizations defenseless until patches are available.
Log4j (2021): The discovery of a critical flaw in the Log4j logging library shook the internet, exposing millions of systems to remote code execution. CISA issued an emergency directive requiring federal agencies to mitigate immediately.
The FBI and CISA regularly warn that nation-state actors aggressively target zero-day flaws to compromise critical infrastructure .
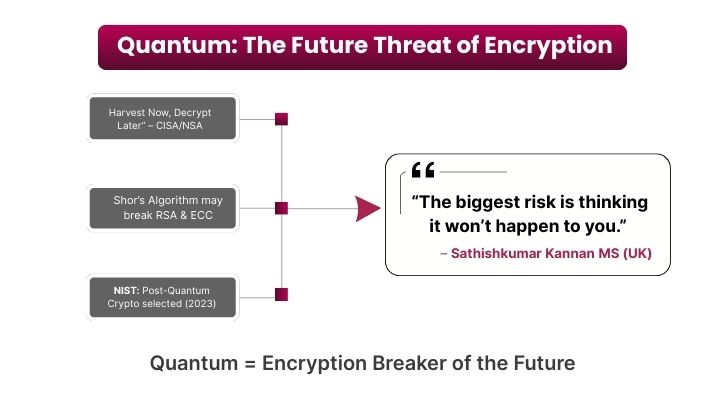
Quantum computers are still emerging, but their future capabilities could break today’s strongest encryption. Hackers are already harvesting encrypted data now, planning to decrypt it later once quantum power is available.
“Harvest Now, Decrypt Later”: CISA and the NSA warn that adversaries are collecting sensitive encrypted communications today, betting on quantum computing breakthroughs to unlock them in the future .
As a CEO, I see cybersecurity not as an expense, but as an investment in trust, continuity, and competitive advantage. In 2025, ignoring cybersecurity is like leaving your office doors wide open at night.
“The biggest risk is thinking it won’t happen to you. The truth is, it already has, or it soon will.”
Businesses that survive and thrive in this new era will be the ones that treat cybersecurity as strategy, not just IT support. The future is here. The threats are real. The time to act is now.