


In today’s digital battlefield, a hacker doesn’t always need an army of tools—sometimes, one well-placed line of malicious code is enough to bring a billion-dollar company to its knees.
From SQL injections that leak millions of credit cards to zero-day exploits crippling global supply chains, these attacks aren’t just theoretical. They’ve been used to steal data, crash networks, halt critical infrastructure, and extort companies worldwide.
As leaders, we can’t rely only on IT teams to “handle cybersecurity.” Understanding the attacks themselves is crucial for making smart investments, setting priorities, and protecting both people and profits.
Here are the 10 most dangerous technical cyberattacks explained simply, with real-world examples.
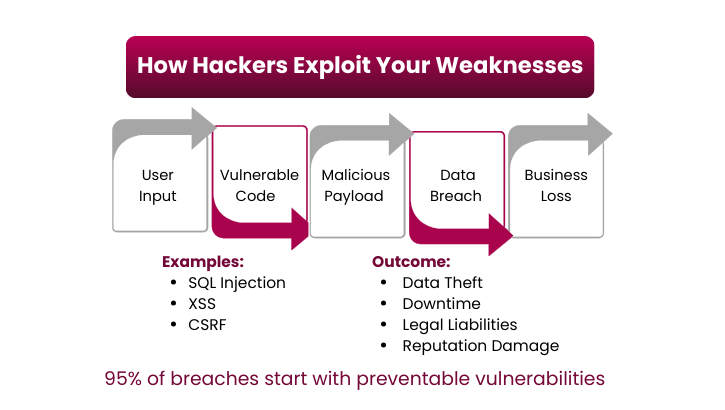
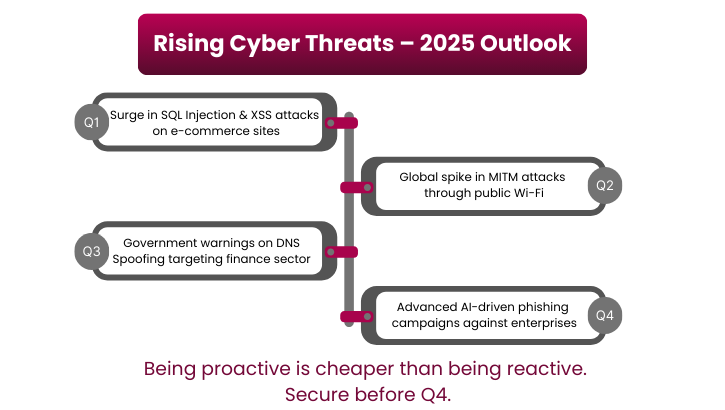
SQL Injection (SQLi) is one of the oldest yet still one of the most dangerous web application attacks. It happens when a hacker inserts malicious SQL commands into input fields (like login forms, search boxes, or contact fields) that aren’t properly validated.
Instead of typing normal input, the attacker types SQL commands that trick the database into revealing, modifying, or deleting information.
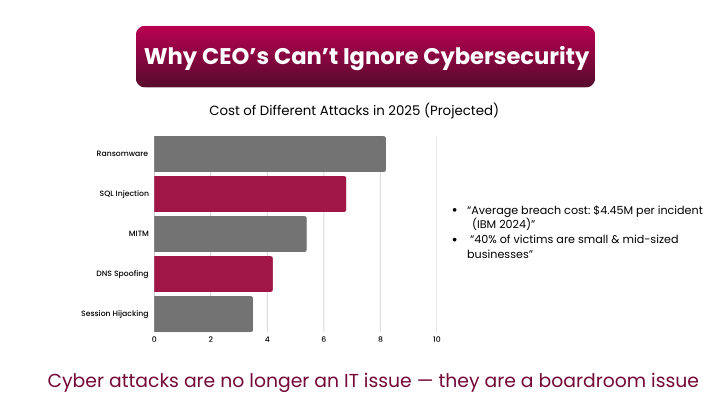
The 2008 Heartland Payment Systems breach, caused by SQL injection, exposed 130 million credit card numbers, making it one of the largest data thefts ever reported.
Cross-Site Scripting (XSS) is a web attack where hackers inject malicious JavaScript into trusted websites. When other users load the page, the script executes in their browser—often without them knowing.
An attacker places malicious code into input fields, comment sections, or URLs. When unsuspecting users visit the page, the code runs as if it came from the legitimate site.
In 2014, eBay suffered a major XSS attack, where listings contained malicious JavaScript that redirected shoppers to phishing sites. This went undetected for months and exposed millions of users .
Cross-Site Request Forgery (CSRF) is an attack that tricks a logged-in user’s browser into carrying out unwanted actions on a web application without their knowledge. Since the user is already authenticated, the site treats the forged request as legitimate.
A hacker lures the victim (via email, malicious link, or embedded form) into unknowingly submitting a request. For example, clicking a hidden link that instructs the bank’s website to transfer money.
Several online banking applications have historically been exploited by CSRF, allowing attackers to trigger unauthorized transactions on behalf of victims.
Directory Traversal, also called Path Traversal, is an attack where hackers manipulate file path inputs to gain access to restricted directories and files on a server. By using special characters like ../, attackers can “climb” out of the intended folder and view sensitive system files.
An application allows users to request files (like images or documents) but doesn’t properly validate the input. Attackers alter the request to fetch critical files such as configuration files or password databases.
Many legacy PHP and Apache-based applications were exploited via directory traversal to expose /etc/passwd on Linux systems, leaking user account information. This attack is listed in the as one of the most common web vulnerabilities.
File Inclusion Attacks occur when a web application allows users to include files without proper validation. These can be Local File Inclusion (LFI) pulling files already on the server or Remote File Inclusion (RFI) loading malicious files from external sources.
A vulnerable parameter (e.g., ?page=home.php) can be manipulated to include sensitive files like /etc/passwd (LFI) or a hacker-controlled script hosted remotely (RFI).
In 2007, a PHP Remote File Inclusion (RFI) vulnerability in a widely used CMS allowed attackers to upload malicious scripts, leading to thousands of compromised websites.
XML External Entity (XXE) attacks exploit vulnerable XML parsers that allow external entity references. Attackers use this to read sensitive files, send requests to internal systems, or even execute malicious code.
An attacker submits XML data containing a malicious entity definition. The vulnerable parser processes it, exposing internal files or enabling further attacks.
In 2017, XXE vulnerabilities were reported in several online services, where attackers could read local files and access backend systems.
Insecure Deserialization occurs when an application accepts untrusted serialized data and deserializes it without proper validation. Attackers can tamper with this data to inject malicious objects, leading to code execution or privilege escalation.
Applications often serialize data (convert objects into storable/transmittable formats) and then later deserialize it. If attackers modify this data before it’s processed, they can execute arbitrary code or manipulate app logic.
In 2017, insecure deserialization vulnerabilities in Apache Struts 2 led to remote code execution exploits, affecting enterprise applications worldwide .
A Man-in-the-Middle (MITM) attack happens when a hacker secretly intercepts and manipulates communication between two parties. The victims believe they’re talking directly to each other, but the attacker is relaying or altering the traffic in between.
MITM is often done through rogue Wi-Fi hotspots, ARP spoofing, or DNS hijacking. For example, a hacker sets up a fake public Wi-Fi named “Free Airport Wi-Fi” and monitors everything victims send through it.
In 2017, security researchers demonstrated MITM attacks over public Wi-Fi, showing how attackers could capture credit card details from unencrypted traffic.
Session Hijacking and Replay Attacks occur when hackers steal or reuse session tokens to impersonate a legitimate user. Instead of cracking a password, the attacker rides on an already-authenticated session.
Web apps issue session IDs or tokens after login. If these tokens are exposed (through insecure cookies, XSS, or packet sniffing), attackers can hijack them. In replay attacks, stolen credentials or tokens are captured and reused to trick the server into accepting the attacker as a valid user.
In 2010, the Firesheep Firefox extension allowed attackers on open Wi-Fi to hijack Facebook and Twitter sessions by stealing session cookies, showing how easily accounts could be compromised. Session attacks are detailed in the OWASP Session Hijacking Guide as one of the most overlooked but dangerous risks in web security.
DNS Spoofing, also called DNS Cache Poisoning, is when attackers corrupt or manipulate the Domain Name System (DNS) to redirect users to malicious websites instead of legitimate ones. Since DNS is the “phonebook of the internet,” poisoning it allows attackers to hijack trust at the root.
Hackers insert false DNS records into a resolver’s cache. For example, instead of directing a user to www.bank.com, the poisoned entry sends them to a fake lookalike controlled by the attacker.
In 2018, attackers hijacked MyEtherWallet’s DNS, redirecting users to a malicious site, and stealing cryptocurrency funds from unsuspecting victims.
I still remember my days working in the UK, when a simple SQL Injection attack exposed how fragile our systems really were. One small vulnerability in a web form suddenly gave outsiders access to sensitive data. It wasn’t just a technical flaw—it was a wake-up call for management, showing how a single missed detail could jeopardize trust, revenue, and reputation.
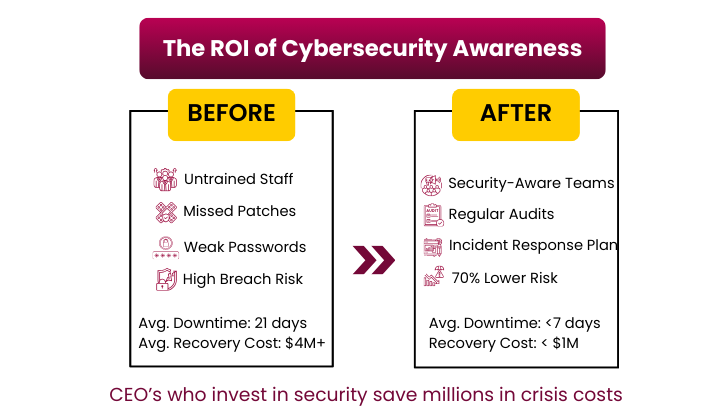
Cybersecurity is no longer about asking “if” you’ll be attacked, but “when”. And when it happens, your company’s survival will depend on the decisions you make today.

As leaders, you don’t need to code or configure firewalls, but you must ensure the right culture, investment, and accountability are in place. Your shareholders, employees, and customers are counting on it.
In the digital battlefield of 2025, attackers are faster, smarter, and more relentless than ever before. But with the right strategy, awareness, and leadership commitment, businesses can turn cybersecurity from a weakness into a competitive advantage.
Remember: it only takes one vulnerability to bring down an empire, but it also takes one decisive leader to stop it.